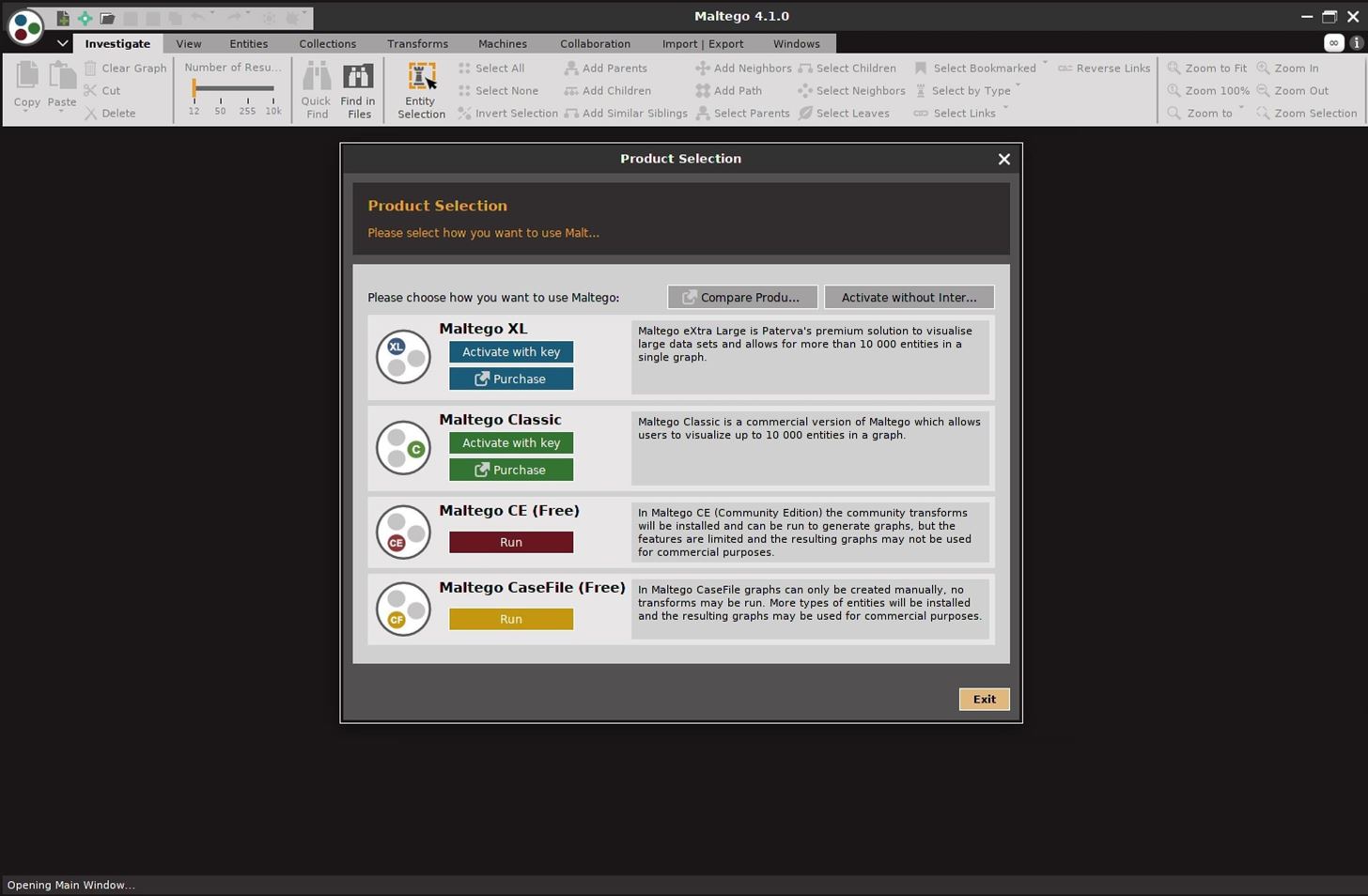
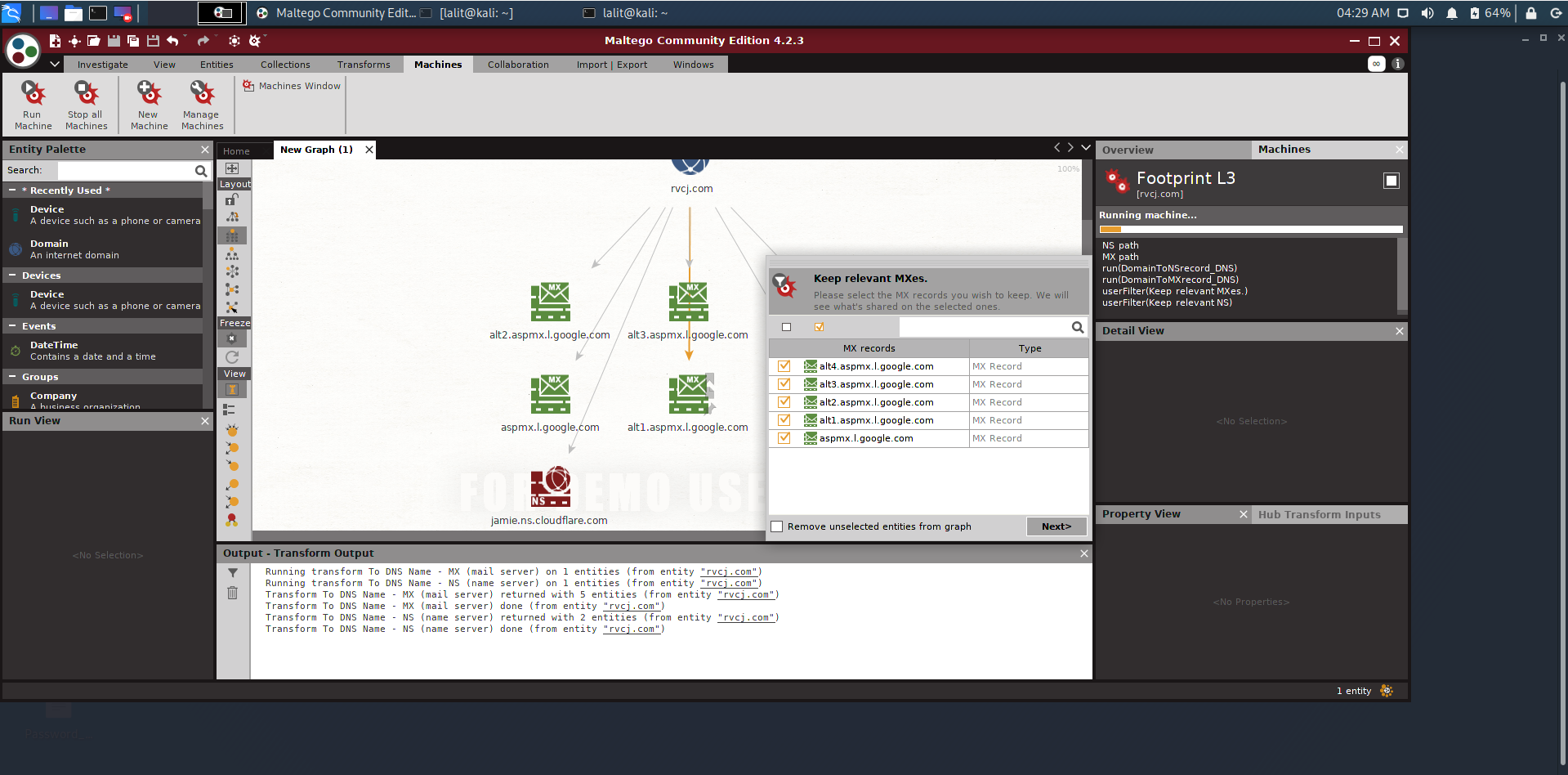
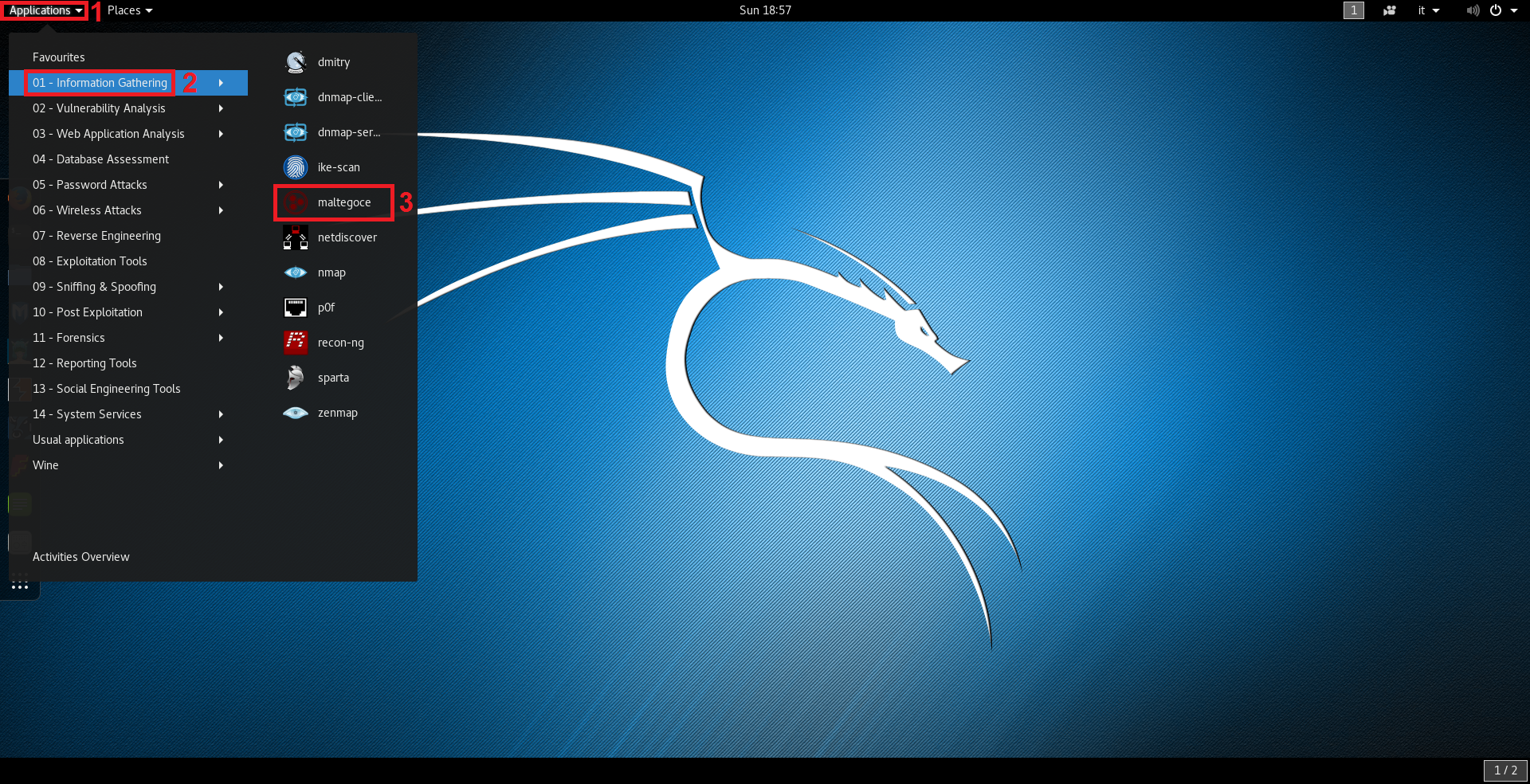
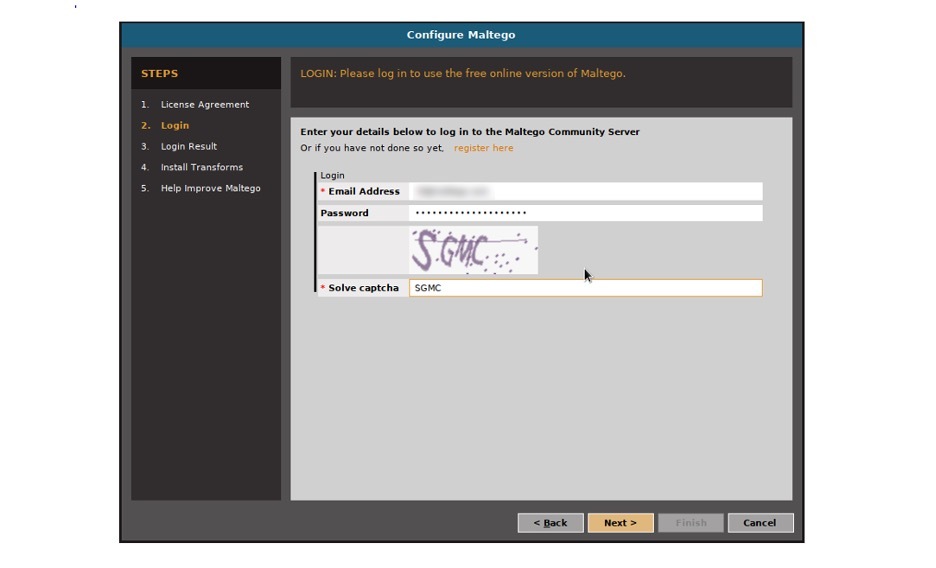
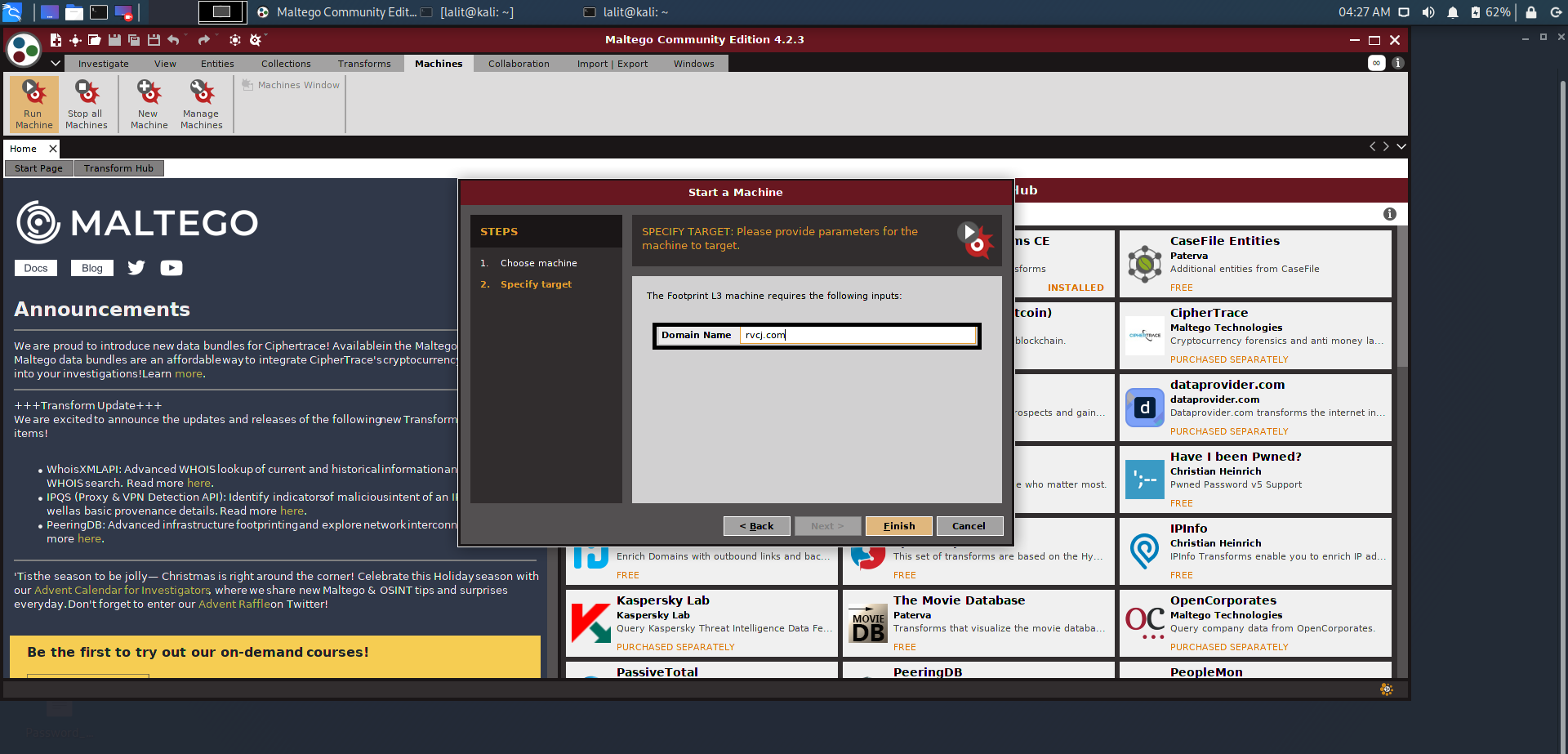
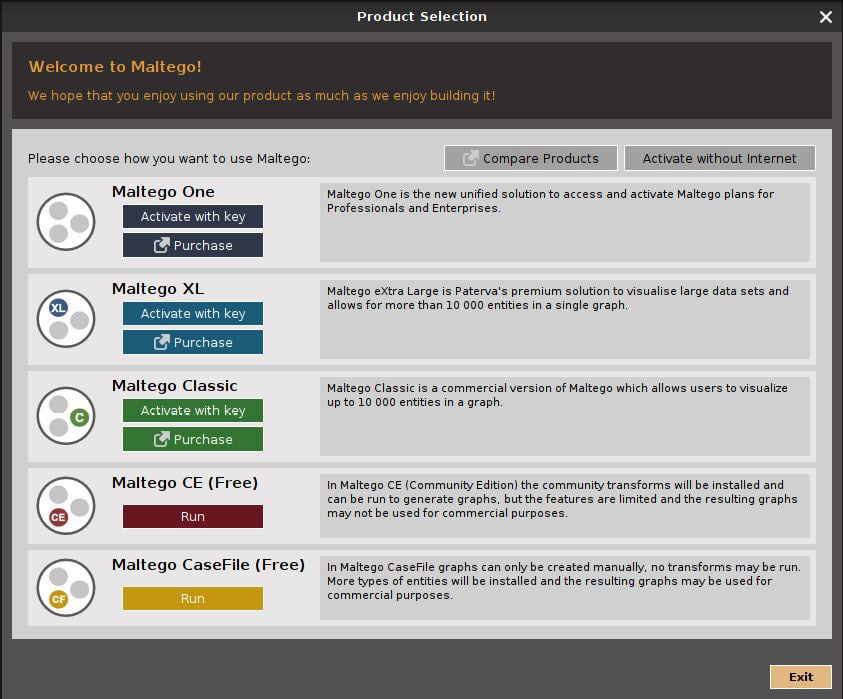
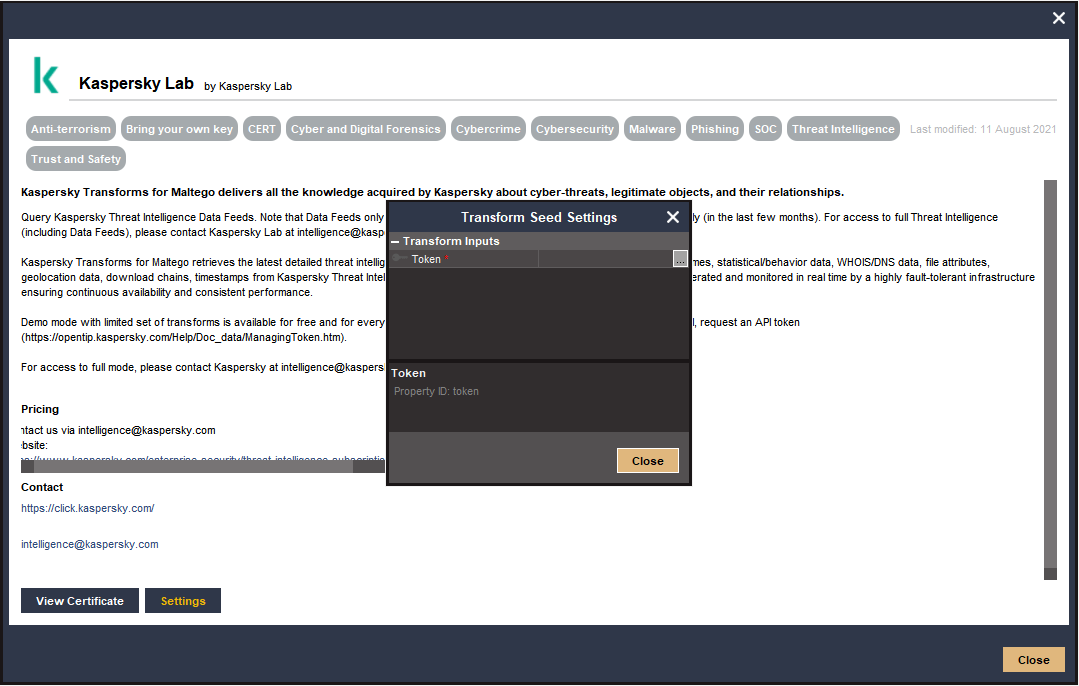
Why am I asked to enter an API key when I have already activated my Maltego client? : Maltego Support

Why am I asked to enter an API key when I have already activated my Maltego client? : Maltego Support
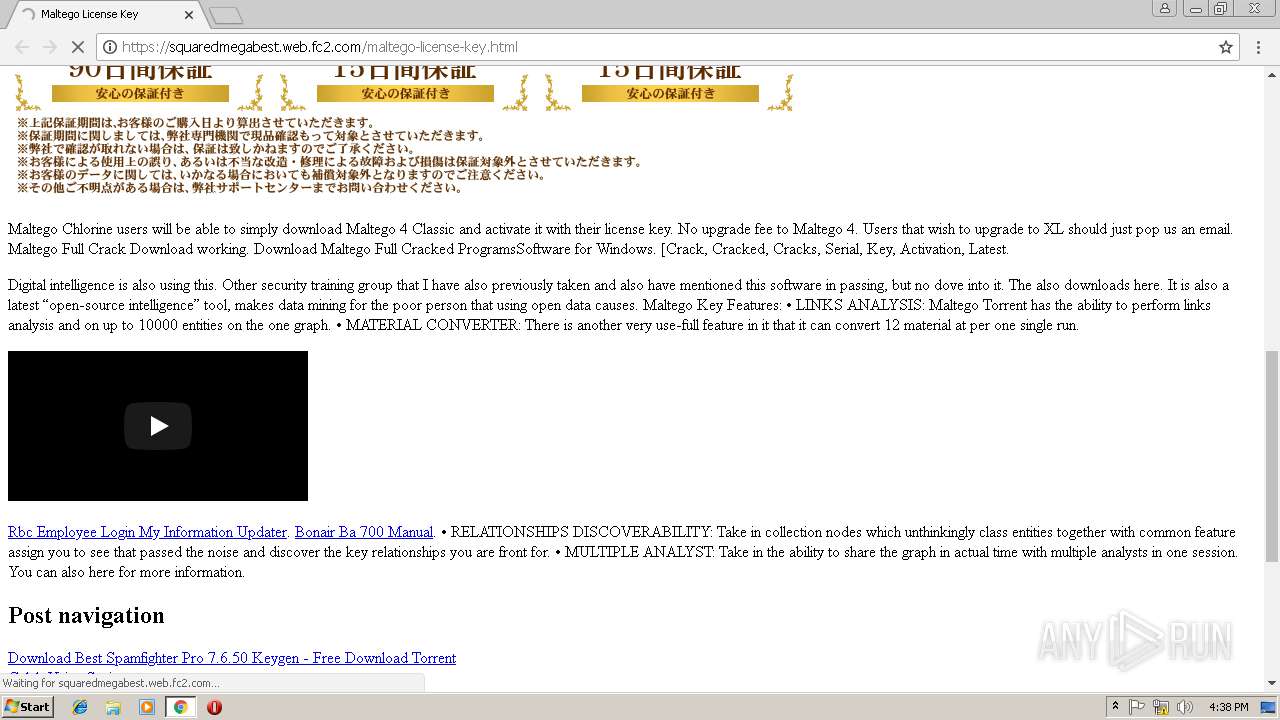
https://squaredmegabest.web.fc2.com/maltego-license-key.html | ANY.RUN - Free Malware Sandbox Online
https://squaredmegabest.web.fc2.com/maltego-license-key.html | ANY.RUN - Free Malware Sandbox Online